对 Azure 存储帐户的每个安全请求都必须经过授权。 默认情况下,你可以使用 Microsoft Entra 凭据或共享密钥授权的帐户访问密钥对请求进行授权。 在这两种类型的授权中,与共享密钥相比,Microsoft Entra ID 提供更高级别的安全性和易用性,是 Azure 推荐的授权方法。 若要要求客户端使用 Microsoft Entra ID 对请求进行授权,你可以禁止使用共享密钥对向存储帐户发出的请求进行授权。
当禁止对某个存储帐户进行共享密钥授权时,Azure 存储将拒绝向该帐户发出的所有使用帐户访问密钥进行授权的后续请求。 只有通过 Microsoft Entra ID 进行授权的安全请求才会成功。 有关使用 Microsoft Entra ID 的详细信息,请参阅授权访问 Azure 存储中的数据。
默认情况下,不会设置存储帐户的“AllowSharedKeyAccess”属性,并且在显式设置此属性之前,它不会返回值。 当属性值为“null”或“true”时,存储帐户允许通过共享密钥授权的请求 。
本文介绍了如何使用 DRAG(Detection-Remediation-Audit-Governance,检测-修正-审核-治理)框架为你的存储帐户持续管理共享密钥授权。
先决条件
在禁止对任何存储帐户的共享密钥访问之前:
- 了解禁用共享密钥如何影响 SAS 令牌
- 考虑与其他 Azure 工具和服务的兼容性
- 请考虑是否需要禁止进行共享密钥授权以使用 Microsoft Entra 条件访问
- 授予文件数据的访问权限或转换 Azure 文件存储工作负载
了解禁用共享密钥如何影响 SAS 令牌
当存储帐户不允许使用共享密钥访问时,Azure 存储会根据 SAS 的类型和请求的目标服务来处理 SAS 令牌。 下表显示了每种类型的 SAS 的授权方式,以及当存储帐户的“AllowSharedKeyAccess”属性为“false”时,Azure 存储将如何处理该 SAS 。
| SAS 类型 | 授权类型 | AllowSharedKeyAccess 为 false 时的行为 |
|---|---|---|
| 用户委托 SAS(仅限 Blob 存储) | Microsoft Entra ID | 允许请求。 Azure 建议尽可能使用用户委托 SAS 以提高安全性。 |
| 服务 SAS | 共享密钥 | 拒绝对所有 Azure 存储服务的请求。 |
| 帐户 SAS | 共享密钥 | 拒绝对所有 Azure 存储服务的请求。 |
Azure 指标和 Azure Monitor 中的日志记录不区分不同类型的共享访问签名。 Azure 指标资源管理器中的 SAS 筛选器和 Azure Monitor 中 Azure 存储日志记录内的 SAS 字段都会报告通过任何类型的 SAS 授权的请求 。 但是,不同类型的共享访问签名以不同的方式获得授权,并且当不允许使用共享密钥访问时,行为会有所不同:
- 服务 SAS 令牌或帐户 SAS 令牌使用共享密钥授权,当 AllowSharedKeyAccess 属性设置为 false时,不允许在对 Blob 存储的请求中使用 。
- 用户委派 SAS 使用 Microsoft Entra ID 授权,当 AllowSharedKeyAccess 属性设置为 false 时,不允许在对 Blob 存储的请求中使用。
评估通向存储帐户的流量时,请记住,检测客户端应用程序使用的授权类型中所述的指标和日志可能包括使用用户委托 SAS 发出的请求。
有关共享访问签名的详细信息,请参阅使用共享访问签名 (SAS) 授予对 Azure 存储资源的有限访问权限。
考虑与其他 Azure 工具和服务的兼容性
许多 Azure 服务使用共享密钥授权来与 Azure 存储进行通信。 如果不允许对存储帐户进行共享密钥授权,这些服务将无法访问该帐户中的数据,并且应用程序可能会受到负面影响。
某些 Azure 工具提供了使用 Microsoft Entra 授权来访问 Azure 存储的选项。 下表列出了一些常用的 Azure 工具,并说明了它们是否可以使用 Microsoft Entra ID 来授权对 Azure 存储的请求。
| Azure 工具 | Microsoft Entra 对 Azure 存储的授权 |
|---|---|
| Azure 门户 | 受支持。 有关使用 Microsoft Entra 帐户从 Azure 门户进行授权的信息,请参阅在 Azure 门户中选择如何授予对 blob 数据的访问权限。 |
| AzCopy | 支持用于 Blob 存储。 有关授权 AzCopy 操作的信息,请参阅 AzCopy 文档中的选择如何提供授权凭据。 |
| Azure 存储资源管理器 | 支持 Blob 存储、队列存储、表存储和 Azure Data Lake Storage。 不支持对文件存储的 Microsoft Entra ID 访问。 请确保选择正确的 Microsoft Entra 租户。 有关详细信息,请参阅存储资源管理器入门 |
| Azure PowerShell | 受支持。 有关如何使用 Microsoft Entra ID 为 blob 或队列操作授权 PowerShell 命令的信息,请参阅使用 Microsoft Entra 凭据运行 PowerShell 命令以访问 blob 数据或使用 Microsoft Entra 凭据运行 PowerShell 命令以访问队列数据。 |
| Azure CLI | 受支持。 有关如何使用 Microsoft Entra ID 授权 Azure CLI 命令来访问 blob 和队列数据的信息,请参阅使用 Microsoft Entra 凭据运行 Azure CLI 命令以访问 blob 或队列数据。 |
| Azure IoT 中心 | 受支持。 有关详细信息,请参阅 IoT 中心对虚拟网络的支持。 |
禁止进行共享密钥授权以使用 Microsoft Entra 条件访问
若要使用 Microsoft Entra 条件访问策略保护 Azure 存储帐户,必须禁止对存储帐户进行共享密钥授权。
授予文件数据的访问权限或转换 Azure 文件存储工作负载
Azure 存储支持针对 Azure 文件存储、Blob 存储、队列存储和表存储请求的 Microsoft Entra 授权。 但是,默认情况下,Azure 门户使用共享密钥授权来访问 Azure 文件共享。 如果不允许对未配置正确 RBAC 分配的存储帐户进行共享密钥授权,则对 Azure 文件存储的请求将失败,并且无法在 Azure 门户中访问 Azure 文件共享。
若要缓解此问题,建议采用以下三种方法之一:
- 按照以下步骤使用 Microsoft Entra 帐户授予文件数据的访问权限,或
- 在禁止通过共享密钥访问帐户之前,将任何 Azure 文件存储数据迁移到单独的存储帐户,或者
- 不要将此设置应用于支持 Azure 文件存储工作负载的存储帐户。
确定允许共享密钥访问的存储帐户
可通过两种方式来确定允许共享密钥访问的存储帐户:
检查多个帐户的共享密钥访问设置
若要检查具有最佳性能的一组存储帐户的共享密钥访问设置,可以使用 Azure 门户中的 Azure Resource Graph 资源管理器。 若要详细了解如何使用 Resource Graph 资源管理器,请参阅快速入门:使用 Azure Resource Graph 资源管理器运行你的第一个 Resource Graph 查询。
在 Resource Graph 资源管理器中运行以下查询会返回存储帐户的列表,并显示每个帐户的共享密钥访问设置:
resources
| where type =~ 'Microsoft.Storage/storageAccounts'
| extend allowSharedKeyAccess = parse_json(properties).allowSharedKeyAccess
| project subscriptionId, resourceGroup, name, allowSharedKeyAccess
在审核模式下配置针对共享密钥访问的 Azure Policy
Azure Policy“存储帐户应阻止共享密钥访问”可阻止具有适当权限的用户配置新的或现有存储帐户以允许共享密钥授权。 在审核模式下配置此策略,以确定允许使用共享密钥授权的存储帐户。 将应用程序更改为使用 Microsoft Entra 而不是共享密钥进行授权后,可以更新策略以阻止允许共享密钥访问。
有关内置策略的详细信息,请参阅内置策略定义列表中的“存储帐户应阻止共享密钥访问”。
为资源范围分配内置策略
在 Azure 门户中,按照以下步骤针对适当范围分配内置策略:
在 Azure 门户中,搜索 Policy 以显示 Azure Policy 仪表板。
在“创作”部分,选择“分配” 。
选择“分配策略”。
在“分配策略”页的“基本信息”选项卡上,在“范围”部分指定策略分配的范围 。 选择“更多”按钮 (...) 以选择订阅和可选资源组。
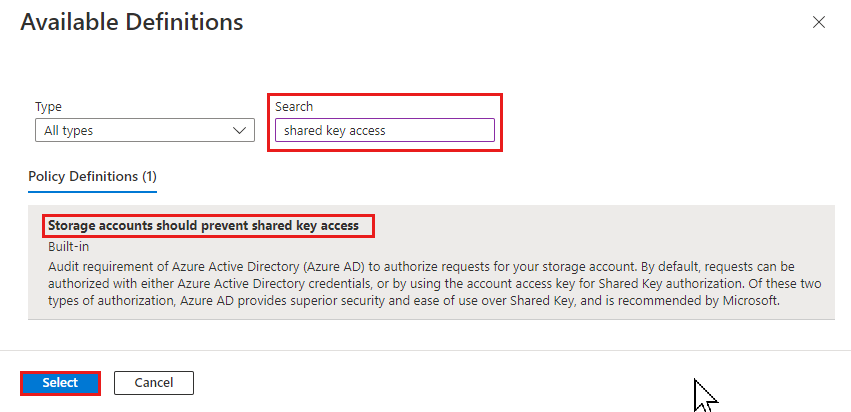
对于“策略定义”字段,选择“更多”按钮 (...),然后在“搜索”字段中输入存储帐户密钥。 选择名为“存储帐户应阻止共享密钥访问”的策略定义。
选择“查看 + 创建” 。
在“查看 + 创建”选项卡上,查看策略分配,然后选择“创建”以将策略定义分配到指定范围。
监视策略的合规性
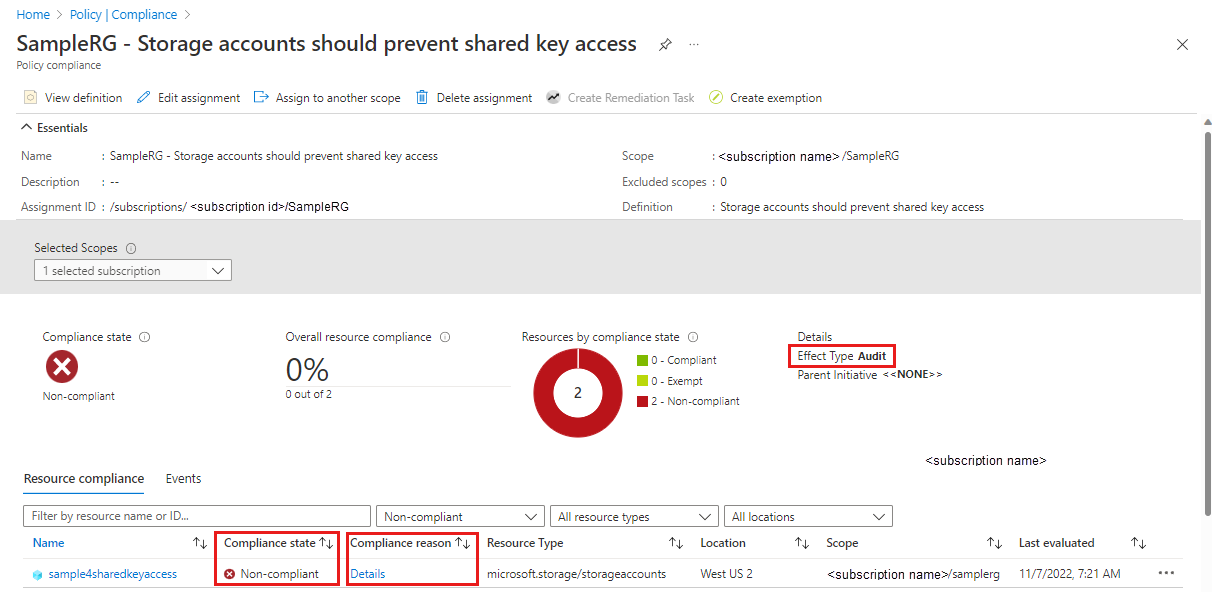
若要监视存储帐户是否符合共享密钥访问策略,请执行以下步骤:
若要详细了解存储帐户不合规的原因,请选择“符合性原因”下的“详细信息”。
检测客户端应用程序使用的授权类型
若要了解在进行此更改之前禁用共享密钥授权可能会对客户端应用程序产生何种影响,请为存储帐户启用日志记录和指标。 然后,你可以分析一段时间内帐户的请求模式,以确定请求的授权方式。
使用指标来确定存储帐户收到的通过共享密钥或共享访问签名 (SAS) 授权的请求数。 使用日志来确定发送这些请求的客户端。
可以通过共享密钥或 Microsoft Entra ID 为 SAS 授权。 有关解释使用共享访问签名发出的请求的详细信息,请参阅了解禁止共享密钥对 SAS 令牌产生的影响。
确定使用共享密钥授权的请求的数量和频率
若要跟踪对存储帐户请求的授权方式,请在 Azure 门户中使用 Azure 指标资源管理器。 若要详细了解指标资源管理器,请参阅使用 Azure Monitor 指标资源管理器分析指标。
按照以下步骤创建一个指标,该指标用于跟踪使用共享密钥或 SAS 发出的请求:
导航到 Azure 门户中的存储帐户。 在“监视”部分下,选择“指标” 。
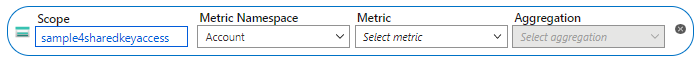
应显示“新建指标”框:
如果未显示此框,请选择“添加指标”。
在“指标”对话框中,指定以下值:
- 将“范围”字段设置为存储帐户的名称。
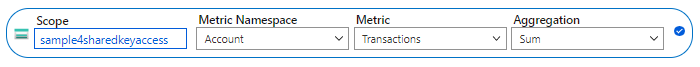
- 将“指标命名空间”设置为“帐户”。 此指标将报告对存储帐户的所有请求。
- 将“指标”字段设置为“事务”。
- 将“聚合”字段设置为“求和”。
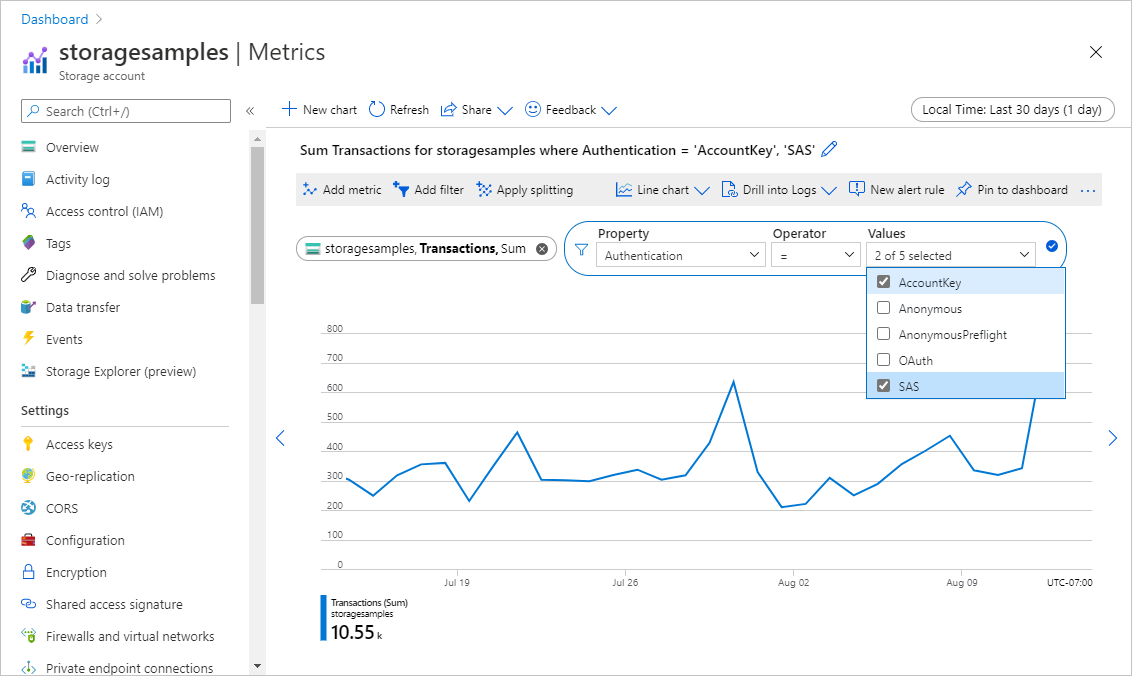
新指标会显示给定时间间隔内针对存储帐户的事务数之和。 生成的指标如下图所示:
接下来,选择“添加筛选器”按钮,为授权类型指标创建筛选器。
在“筛选器”对话框中,指定以下值:
- 将属性值设置为“身份验证”。
- 将“运算符”字段设置为等号 (=)。
- 在“值”字段中,选择“帐户密钥”和“SAS” 。
在右上角,选择要查看指标的时间范围。 还可以通过指定从 1 分钟到 1 个月的时间间隔,来指示请求聚合粒度。 例如,将“时间范围”设置为30天,并将“时间粒度”设置为 1 天,以查看过去 30 天内按天聚合的请求 。
配置指标后,对存储帐户的请求将开始显示在图表上。 下图显示了使用共享密钥授权或使用 SAS 令牌发出的请求。 在过去的 30 天内,请求按天聚合。
你还可以配置警报规则,让系统在对针对存储帐户发出的匿名请求达到一定数量时通知你。 有关详细信息,请参阅使用 Azure Monitor 创建、查看和管理指标警报。
分析日志以识别使用共享密钥或 SAS 为请求授权的客户端
Azure 存储日志会捕获有关针对存储帐户发出的请求的详细信息,包括请求的授权方式。 可以分析日志以确定哪些客户端正在使用共享密钥或 SAS 令牌为请求授权。
若要记录针对 Azure 存储帐户发出的请求以评估这些请求的授权方式,可以使用 Azure Monitor 中的 Azure 存储日志记录。 有关详细信息,请参阅监视 Azure 存储。
Azure Monitor 中的 Azure 存储日志记录支持使用日志查询来分析日志数据。 若要查询日志,可以使用 Azure Log Analytics 工作区。 若要详细了解日志查询,请参阅教程:Log Analytics 查询入门。
在 Azure 门户中创建诊断设置
若要使用 Azure Monitor 记录 Azure 存储数据并使用 Azure Log Analytics 对其进行分析,必须先创建一项诊断设置,用于指示要记录其数据的请求类型和存储服务。 配置存储帐户的日志记录后,日志将在 Log Analytics 工作区中提供。 若要创建工作区,请参阅在 Azure 门户中创建 Log Analytics 工作区。
若要了解如何在 Azure 入口中创建诊断设置,请参阅在 Azure Monitor 中创建诊断设置。
有关 Azure Monitor 的 Azure 存储日志中可用字段的参考,请参阅资源日志。
查询使用共享密钥或 SAS 发出的请求的日志
Azure Monitor 中的 Azure 存储日志包括用于对存储帐户发出请求的授权类型。 若要检索过去 7 天发出的、使用共享密钥或 SAS 授权的请求的日志,请打开你的 Log Analytics 工作区。 接下来,将以下查询粘贴到新的日志查询中并运行该查询。 此查询将显示最频繁地发送使用共享密钥或 SAS 授权的请求的 10 个 IP 地址:
StorageBlobLogs
| where AuthenticationType in ("AccountKey", "SAS") and TimeGenerated > ago(7d)
| summarize count() by CallerIpAddress, UserAgentHeader, AccountName
| top 10 by count_ desc
还可以基于此查询配置警报规则,以接收有关已使用共享密钥或 SAS 为请求授权的通知。 有关详细信息,请参阅使用 Azure Monitor 创建、查看和管理日志警报。
修正通过共享密钥进行的授权
在分析对存储帐户发出的请求的授权方式后,可以采取措施来阻止通过共享密钥进行访问。 但首先,你需要将使用共享密钥授权的所有应用程序更新为改用 Microsoft Entra ID。 可以按照检测客户端应用程序使用的授权类型所述的方法监视日志和指标,以便对转换进行跟踪。 若要详细了解如何使用 Microsoft Entra ID 访问存储帐户中的数据,请参阅授权访问 Azure 存储中的数据。
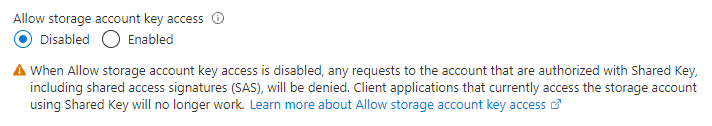
确信可以安全地拒绝通过共享密钥授权的请求时,可以将存储帐户的“AllowSharedKeyAccess”属性设置为“false” 。
警告
如果任何客户端当前正在使用共享密钥访问存储帐户中的数据,则 Azure 建议将这些客户端迁移到 Microsoft Entra ID,然后再禁止对存储帐户的共享密钥访问。
允许或禁止共享密钥访问的权限
若要为存储帐户设置“AllowSharedKeyAccess”属性,用户必须具有创建和管理存储帐户的权限。 提供这些权限的 Azure 基于角色的访问控制 (Azure RBAC) 角色包含 Microsoft.Storage/storageAccounts/write 或 Microsoft.Storage/storageAccounts/* 操作。 具有此操作的内置角色包括:
这些角色未提供通过 Microsoft Entra ID 访问存储帐户中数据的访问权限。 但是,它们包含 Microsoft.Storage/storageAccounts/listkeys/action,可以授予对帐户访问密钥的访问权限。 借助此权限,用户可以使用帐户访问密钥访问存储帐户中的所有数据。
角色分配的范围必须设定为存储帐户级别或更高级别,以允许用户启用或禁用对存储帐户的共享密钥访问。 有关角色范围的详细信息,请参阅了解 Azure RBAC 的范围。
请注意,仅向需要能够创建存储帐户或更新其属性的用户分配这些角色。 使用最小特权原则确保用户拥有完成任务所需的最少权限。 有关使用 Azure RBAC 管理访问权限的详细信息,请参阅 Azure RBAC 最佳做法。
注意
经典订阅管理员角色“服务管理员”和“共同管理员”具有 Azure 资源管理器所有者角色的等效权限。 所有者角色包括所有操作,因此具有这些管理角色之一的用户也可以创建和管理存储帐户。 有关详细信息,请参阅 Azure 角色、Azure AD 角色和经典订阅管理员角色。
禁用共享密钥授权
使用具有必需权限的帐户,借助 PowerShell 或使用 Azure CLI 在 Azure 门户中禁用共享密钥授权。
若要在 Azure 门户中禁止对存储帐户的共享密钥授权,请按照以下步骤操作:
禁用共享密钥授权后,使用共享密钥授权对存储帐户发出的请求将失败,错误代码为 403(禁止访问)。 Azure 存储会返回错误,指示不允许对存储帐户进行基于密钥的授权。
仅使用 Azure 资源管理器部署模型的存储帐户支持 AllowSharedKeyAccess 属性。 有关哪些存储帐户使用 Azure 资源管理器部署模型的信息,请参阅存储帐户的类型。
验证是否不允许使用共享密钥访问
要验证是否已不再允许共享密钥授权,可以使用以下命令查询 Azure 存储帐户设置。 请将括号中的占位符值替换为你自己的值。
az storage account show \
--name <storage-account-name> \
--resource-group <resource-group-name> \
--query "allowSharedKeyAccess"
如果存储帐户不允许使用共享密授权,该命令将返回 false。
注意
匿名请求是未经授权的,如果已将存储帐户和容器配置为匿名读取访问,则该请求将继续。 有关详细信息,请参阅配置对容器和 Blob 的匿名读取访问。
监视 Azure Policy 的合规性
禁止对所需存储帐户的共享密钥访问后,请继续监视之前创建的策略以确保持续满足合规性。 根据监视结果,根据需要采取适当的操作,包括更改策略的范围、禁止对更多帐户的共享密钥访问,或者在需要更多时间进行修正的情况下允许对帐户的共享密钥访问。
更新 Azure Policy 以阻止允许共享密钥访问
若要为策略“存储帐户应阻止共享密钥访问”强制执行之前创建的 Azure Policy 分配,请将策略分配的“效果”更改为“拒绝”,以阻止授权用户允许对存储帐户的共享密钥访问。 若要更改策略的效果,请执行以下步骤:
在 Azure Policy 仪表板上,找到并选择之前创建的策略分配。
选择“编辑分配”。
转到“参数”选项卡。
取消选中“仅显示需要输入或评审的参数”复选框。
在“效果”下拉列表中,将“审核”更改为“拒绝”,然后选择“查看 + 保存”。
在“查看 + 保存”选项卡上,查看更改,然后选择“保存”。
注意
策略更改最多可能需要 30 分钟才能生效。