AKS 托管的 Azure Active Directory (Azure AD) 集成简化了 Azure AD 集成过程。 以前,你需要创建客户端和服务器应用,并且 Azure AD 租户必须授予“目录读取”权限。 现在,AKS 资源提供程序将为你管理客户端和服务器应用。
Azure AD 身份验证概述
群集管理员可以根据用户的标识或目录组成员身份来配置 Kubernetes 基于角色的访问控制 (Kubernetes RBAC)。 使用 OpenID Connect 向 AKS 群集提供 Azure AD 身份验证。 OpenID Connect 是构建在 OAuth 2.0 协议顶层的标识层。 有关 OpenID Connect 的详细信息,请参阅 Open ID Connect 文档。
在 Azure AD 文档中详细了解 Azure AD 集成流程。
限制
- 无法禁用 AKS 托管的 Azure AD 集成。
- 不支持将 AKS 托管的 Azure AD 集成式群集更改为旧版 Azure AD。
- AKS 托管的 Azure AD 集成不支持未启用 Kubernetes RBAC 的群集。
先决条件
在开始之前,请确保满足以下先决条件:
重要
必须使用最低版本为 1.18.1 的 kubectl,或者使用 kubelogin。 Kubernetes 和 kubectl 的次版本之间的差不应超过 1 个版本。 如果未使用正确的版本,你会遇到身份验证问题。
使用以下命令安装 kubectl 和 kubelogin:
sudo az aks install-cli
kubectl version --client
kubelogin --version
对于其他操作系统,请遵循这些说明。
开始之前
需要为群集创建一个 Azure AD 组。 此组将在群集上注册为管理员组,以授予群集管理员权限。 可以使用现有 Azure AD 组,也可以创建一个新组。 请务必记下 Azure AD 组的对象 ID。
# List existing groups in the directory
az ad group list --filter "displayname eq '<group-name>'" -o table
使用以下命令为群集管理员创建新的 Azure AD 组:
# Create an Azure AD group
az ad group create --display-name myAKSAdminGroup --mail-nickname myAKSAdminGroup
创建已启用 Azure AD 的 AKS 群集
创建 Azure 资源组。
az group create --name myResourceGroup --location chinaeast2创建一个 AKS 群集,并使用
az aks create命令为 Azure AD 组启用管理访问权限。az aks create -g myResourceGroup -n myManagedCluster --enable-aad --aad-admin-group-object-ids <id> [--aad-tenant-id <id>]成功创建 AKS 托管的 Azure AD 群集后,响应正文中会包含以下部分:
"AADProfile": { "adminGroupObjectIds": [ "5d24****-****-****-****-****afa27aed" ], "clientAppId": null, "managed": true, "serverAppId": null, "serverAppSecret": null, "tenantId": "72f9****-****-****-****-****d011db47" }
访问已启用 Azure AD 的群集
使用 Azure AD 定义的组访问群集之前,需要 Azure Kubernetes 服务群集用户内置角色。
获取用于访问群集的用户凭据。
az aks get-credentials --resource-group myResourceGroup --name myManagedCluster按照说明进行登录。
使用
kubectl get nodes命令查看群集中的节点。kubectl get nodes设置 Azure 基于角色的访问控制 (Azure RBAC),以配置群集的其他安全组。
排查 Azure AD 的访问权限问题
重要
本部分中介绍的步骤会绕过正常的 Azure AD 组身份验证。 请仅在紧急情况下使用它们。
如果你被永久阻止,不能访问具有群集访问权限的有效 Azure AD 组,你仍可以获取管理员凭据以直接访问群集。 你需要具有访问 Azure Kubernetes 服务群集管理员内置角色的权限。
az aks get-credentials --resource-group myResourceGroup --name myManagedCluster --admin
在现有群集上启用 AKS 托管的 Azure AD 集成
可以在现有的启用了 Kubernetes RBAC 的群集上启用 AKS 托管的 Azure AD 集成。 确保将管理员组设置为在群集上保留访问权限。
az aks update -g MyResourceGroup -n MyManagedCluster --enable-aad --aad-admin-group-object-ids <id-1> [--aad-tenant-id <id>]
成功激活 AKS 托管的 Azure AD 群集后,响应正文中会包含以下部分:
"AADProfile": {
"adminGroupObjectIds": [
"5d24****-****-****-****-****afa27aed"
],
"clientAppId": null,
"managed": true,
"serverAppId": null,
"serverAppSecret": null,
"tenantId": "72f9****-****-****-****-****d011db47"
}
按照此处的步骤操作,再次下载用户凭据以访问群集。
升级到 AKS 托管的 Azure AD 集成
如果群集使用旧式 Azure AD 集成,可以通过运行以下命令升级到 AKS 托管的 Azure AD 集成:
az aks update -g myResourceGroup -n myManagedCluster --enable-aad --aad-admin-group-object-ids <id> [--aad-tenant-id <id>]
成功迁移 AKS 托管的 Azure AD 群集后,响应正文中会包含以下部分:
"AADProfile": {
"adminGroupObjectIds": [
"5d24****-****-****-****-****afa27aed"
],
"clientAppId": null,
"managed": true,
"serverAppId": null,
"serverAppSecret": null,
"tenantId": "72f9****-****-****-****-****d011db47"
}
要访问群集,请按照《访问已启用 Azure AD 的群集》中的步骤更新 kubeconfig。
通过 kubelogin 进行非交互式登录
有一些当前无法通过 kubectl 执行的非交互式方案,例如持续集成管道。 可以使用 kubelogin 通过非交互式服务主体凭据连接到群集。
禁用本地帐户
在部署 AKS 群集时,本地帐户在默认情况下处于启用状态。 即使是在启用 RBAC 或 Azure AD 集成时,--admin 访问权限也仍作为一个不可审核的后门选项存在。 可以使用参数 disable-local-accounts 禁用本地帐户。 为托管群集 API 添加了 properties.disableLocalAccounts 字段,以指示该功能是否已在群集上启用。
注意
在启用了 Azure AD 集成的群集上,已分配到
aad-admin-group-object-ids指定的 Azure AD 管理员组的用户仍可以使用非管理员凭据获得访问权限。 在未启用 Azure AD 集成且properties.disableLocalAccounts设置为true的群集上,使用用户凭据或管理员凭据尝试身份验证都将失败。在用户可能已在其中使用本地帐户进行身份验证的现有 AKS 群集上禁用本地用户帐户之后,管理员必须轮换群集证书以撤销他们可能有权访问的证书。 如果这是新群集,则无需任何操作。
创建没有本地帐户的新群集
若要新建没有任何本地帐户的 AKS 群集,请使用带 disable-local-accounts 标志的 az aks create 命令。
az aks create -g <resource-group> -n <cluster-name> --enable-aad --aad-admin-group-object-ids <aad-group-id> --disable-local-accounts
在输出中,检查 properties.disableLocalAccounts 字段的设置是否为 true,以确认已禁用了本地帐户。
"properties": {
...
"disableLocalAccounts": true,
...
}
尝试获取管理员凭据的操作会失败,并且会显示错误消息,指示该功能阻止访问:
az aks get-credentials --resource-group <resource-group> --name <cluster-name> --admin
Operation failed with status: 'Bad Request'. Details: Getting static credential isn't allowed because this cluster is set to disable local accounts.
在现有群集上禁用本地帐户
若要在现有 AKS 群集上禁用本地帐户,请使用带有 az aks update 参数的 disable-local-accounts 命令。
az aks update -g <resource-group> -n <cluster-name> --enable-aad --aad-admin-group-object-ids <aad-group-id> --disable-local-accounts
在输出中,检查 properties.disableLocalAccounts 字段的设置是否为 true,以确认已禁用了本地帐户。
"properties": {
...
"disableLocalAccounts": true,
...
}
尝试获取管理员凭据的操作会失败,并且会显示错误消息,指示该功能阻止访问:
az aks get-credentials --resource-group <resource-group> --name <cluster-name> --admin
Operation failed with status: 'Bad Request'. Details: Getting static credential isn't allowed because this cluster is set to disable local accounts.
在现有群集上重新启用本地帐户
AKS 支持使用 enable-local 参数在现有群集上启用已禁用的本地帐户。
az aks update -g <resource-group> -n <cluster-name> --enable-aad --aad-admin-group-object-ids <aad-group-id> --enable-local
在输出中,检查 properties.disableLocalAccounts 字段的设置是否为 false,以确认已重新启用了本地帐户。
"properties": {
...
"disableLocalAccounts": false,
...
}
尝试获取管理员凭据的操作会成功:
az aks get-credentials --resource-group <resource-group> --name <cluster-name> --admin
Merged "<cluster-name>-admin" as current context in C:\Users\<username>\.kube\config
通过 Azure AD 和 AKS 使用条件访问
将 Azure AD 与 AKS 群集集成后,还可以使用条件访问来控制对群集的访问。
注意
Azure AD 条件访问是一项 Azure AD 高级版功能。
创建要用于 AKS 的示例条件访问策略:
- 在 Azure 门户中,转到“Azure Active Directory”页面,然后选择“企业应用程序”。
- 选择“条件访问”>“策略”>“新建策略”。

- 输入策略的名称,例如 aks-policy。
- 在“分配”下,选择“用户和组”。 选择要将策略应用到的用户和组。 在此示例中,请选择对你的群集拥有管理员访问权限的同一个 Azure AD 组。
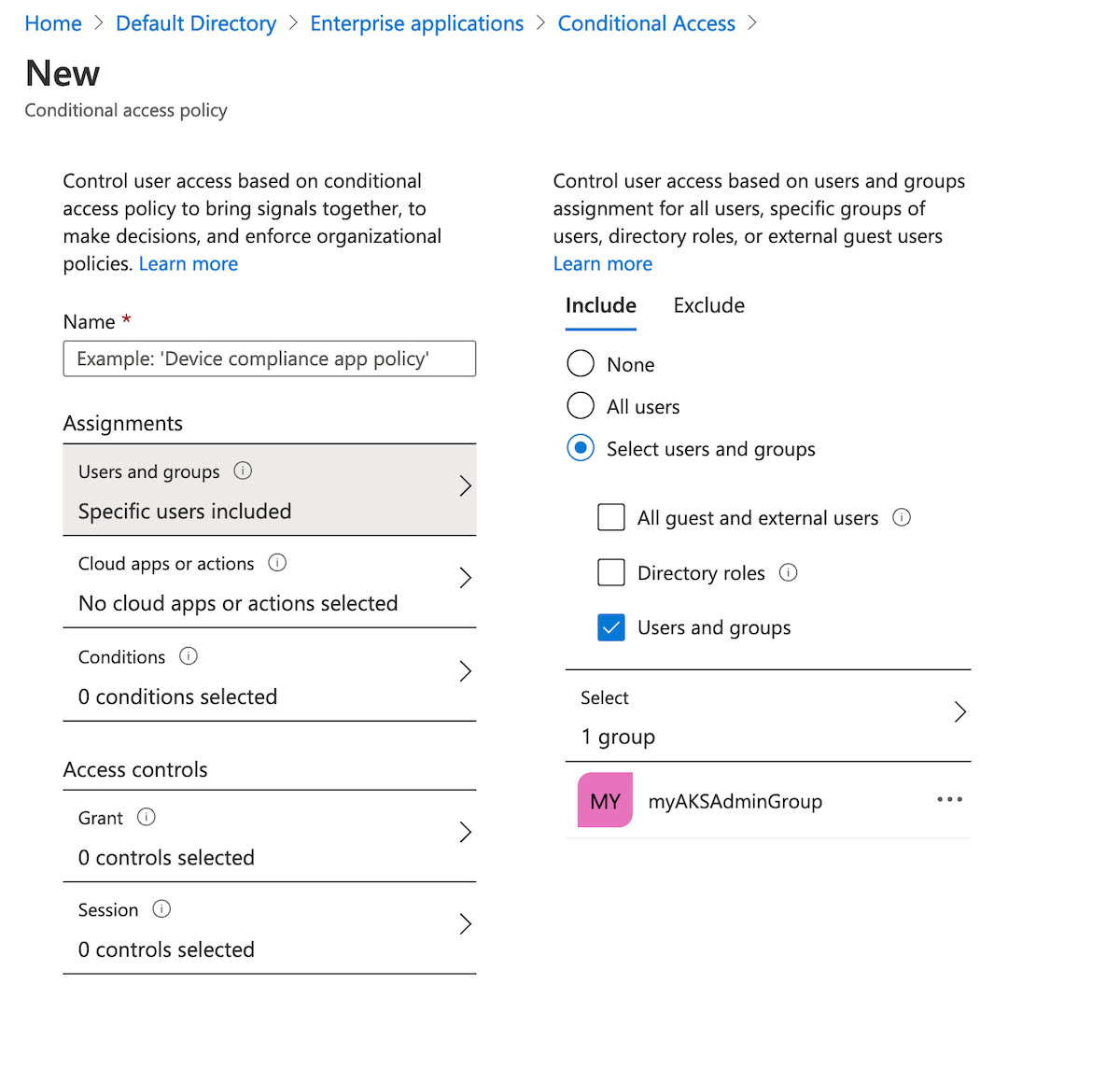
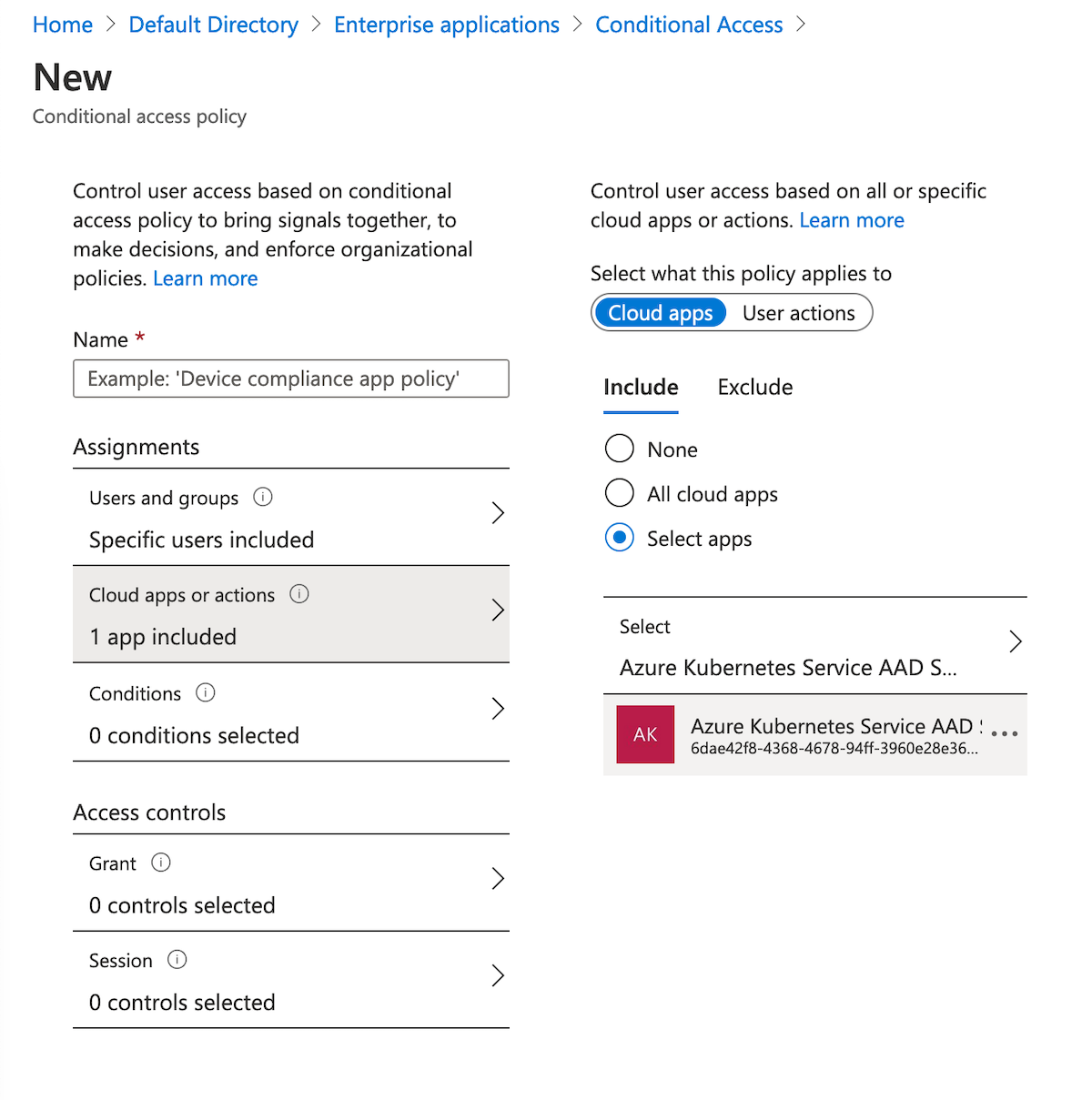
- 在“云应用或操作”“包括”下,选择“选择应用”。 搜索“Azure Kubernetes 服务”,然后选择“Azure Kubernetes 服务 AAD 服务器”。
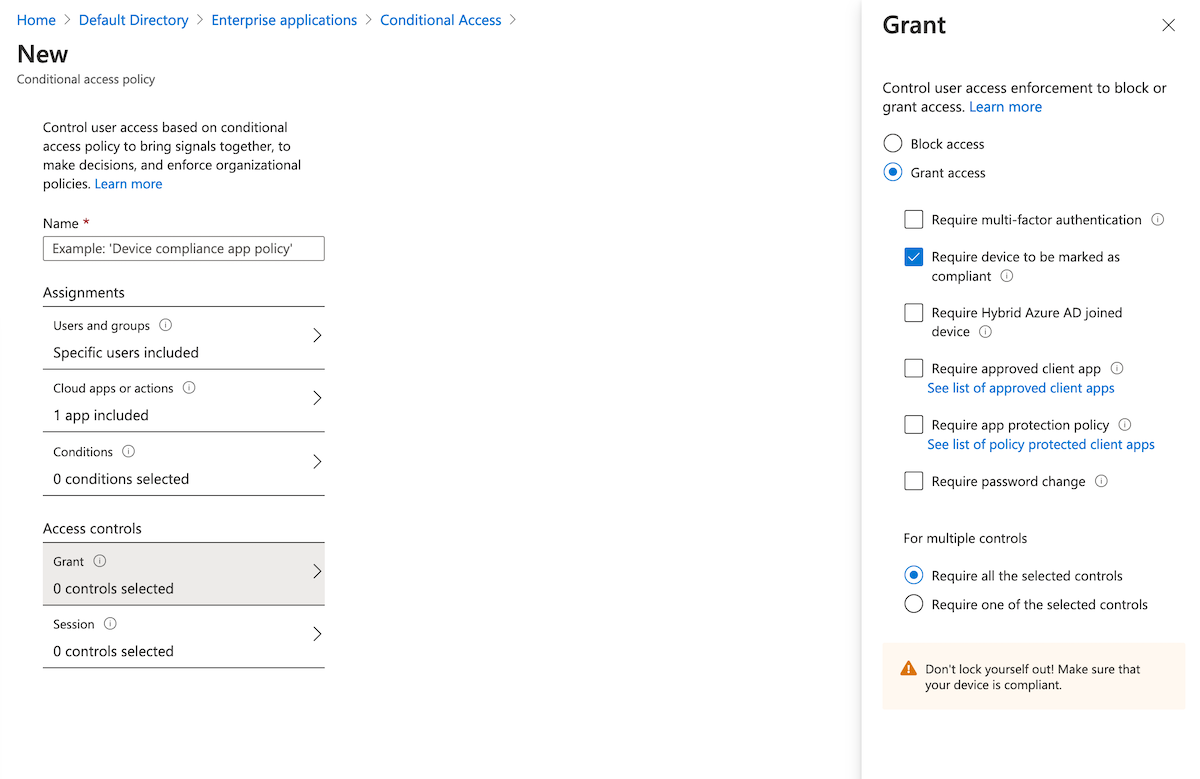
- 在“访问控制 > 授予”下,依次选择“授予访问权限”、“要求将设备标记为合规”和“需要所有已选控制”。
- 确认设置,将“启用策略”设置为“开”,然后选择“创建”。

创建条件访问策略后,验证是否已成功列出该策略:
使用
az aks get-credentials命令获取用户凭据以访问群集。az aks get-credentials --resource-group myResourceGroup --name myManagedCluster按照说明进行登录。
使用
kubectl get nodes命令查看群集中的节点。kubectl get nodes在 Azure 门户中,导航到“Azure Active Directory”并选择“企业应用程序”>“活动”>“登录”。
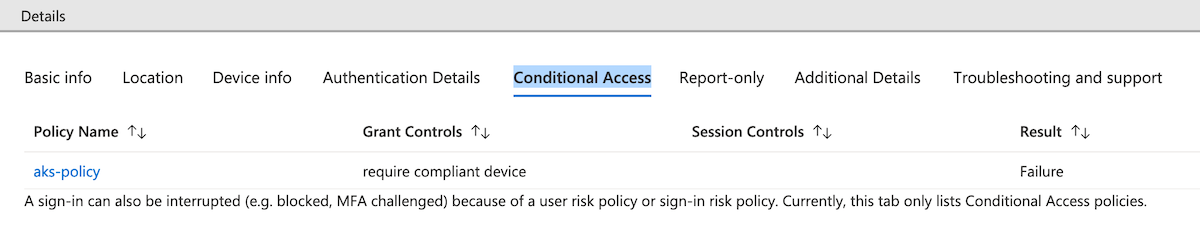
在“条件访问列下,应会看到“成功”状态。 选择该事件,然后选择“条件访问”选项卡。将会列出你的条件访问策略。
使用 Azure AD 和 AKS 配置即时群集访问
用于群集访问控制的另一个选项是对即时请求使用 Privileged Identity Management (PIM)。
注意
PIM 是一个需要 Premium P2 SKU 的 Azure AD Premium 功能。 有关 Azure AD SKU 的详细信息,请参阅定价指南。
使用 AKS 托管的 Azure AD 集成将即时访问请求与 AKS 群集集成:
在 Azure 门户中,转到“Azure Active Directory”并选择“属性”。
注意在“租户 ID”下列出的值。 在稍后的步骤中,将会引用该值作为
<tenant-id>。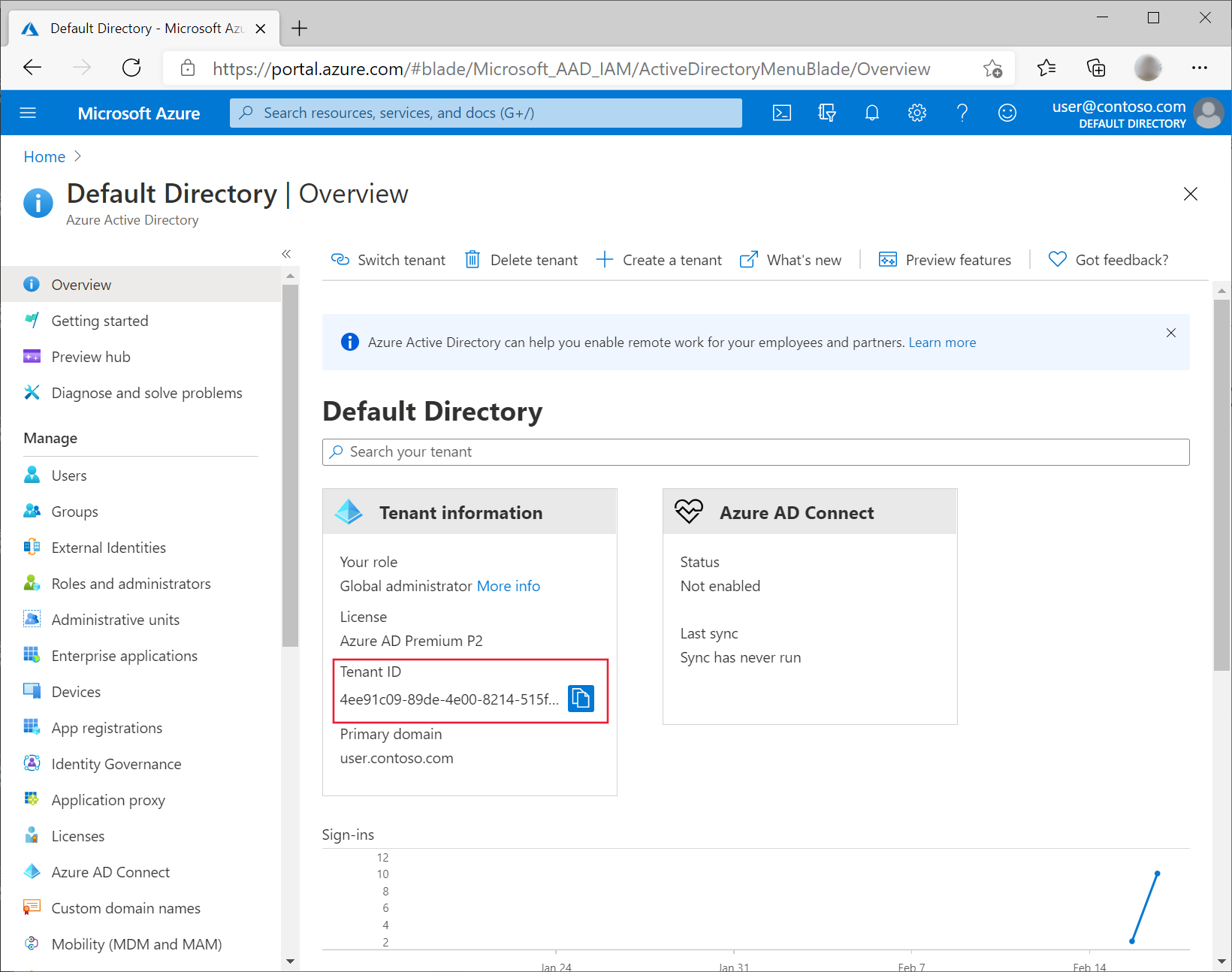
选择“组”>“新建组”。
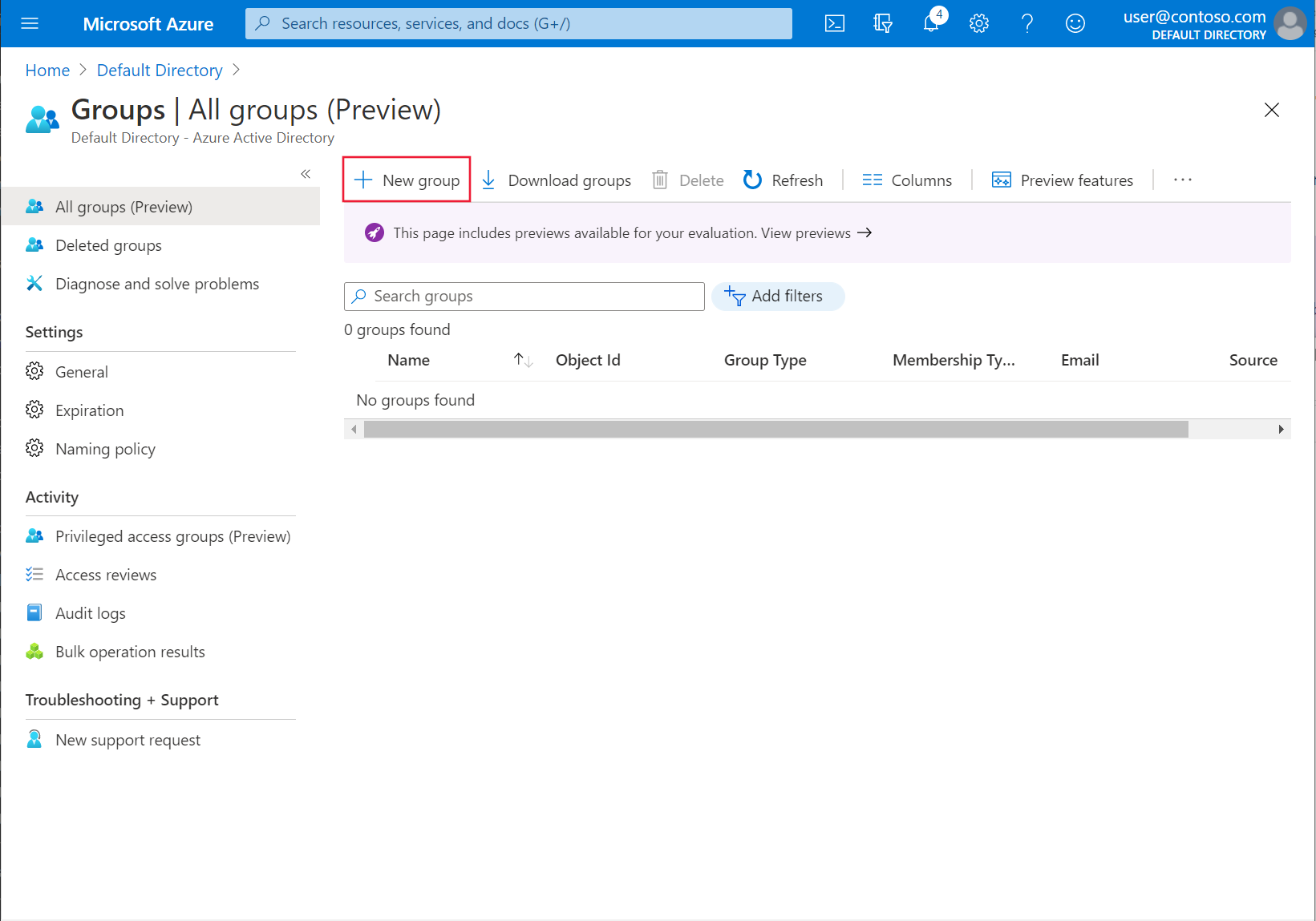
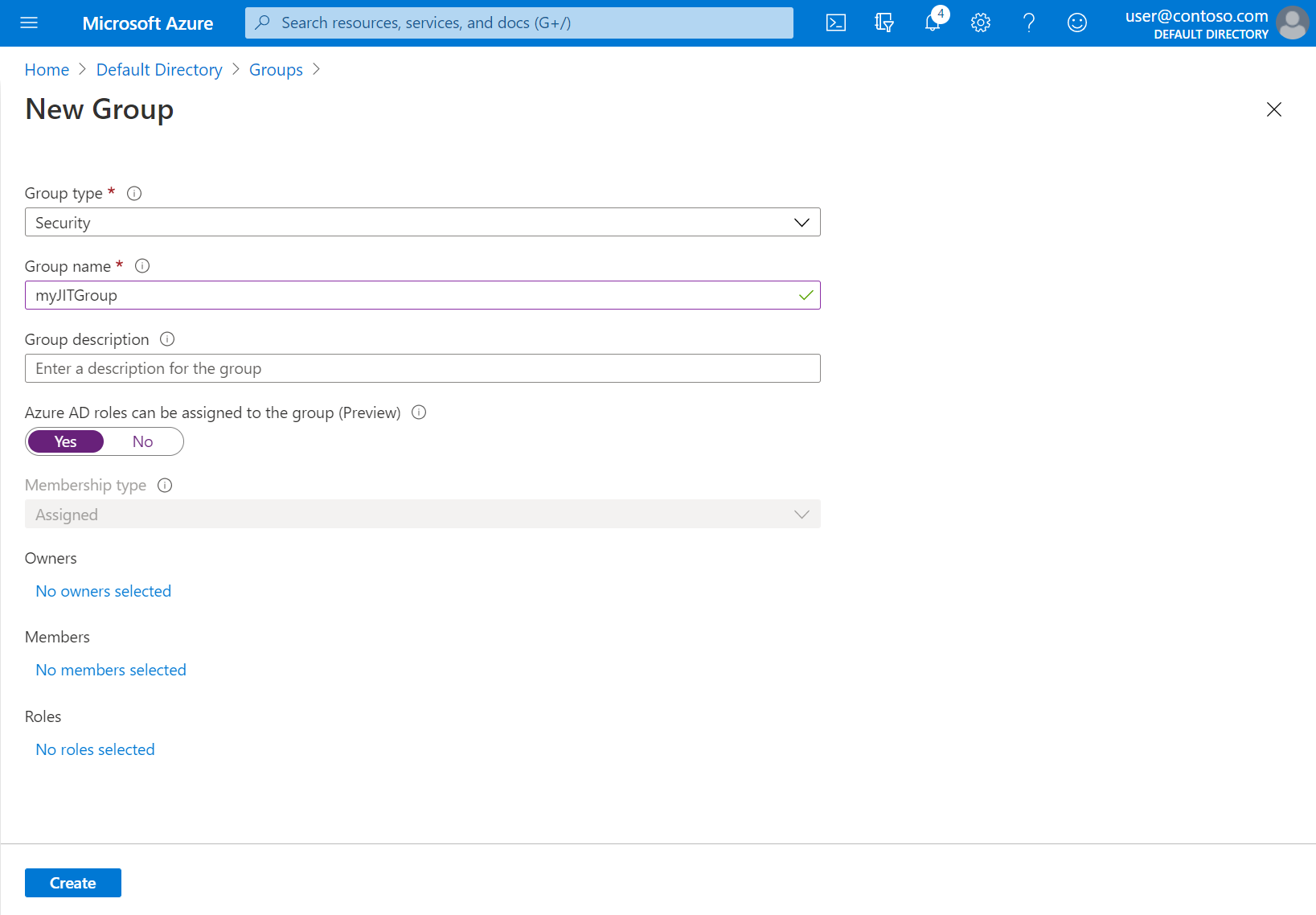
检查是否已选择组类型“安全性”并指定组名称,例如 myJITGroup。 在“可将 Azure AD 角色分配到此组(预览版)”下选择“是”,然后选择“创建”。
在“组”页上选择刚刚创建的组,并记下“对象 ID”。 在稍后的步骤中,会将其引用为
<object-id>。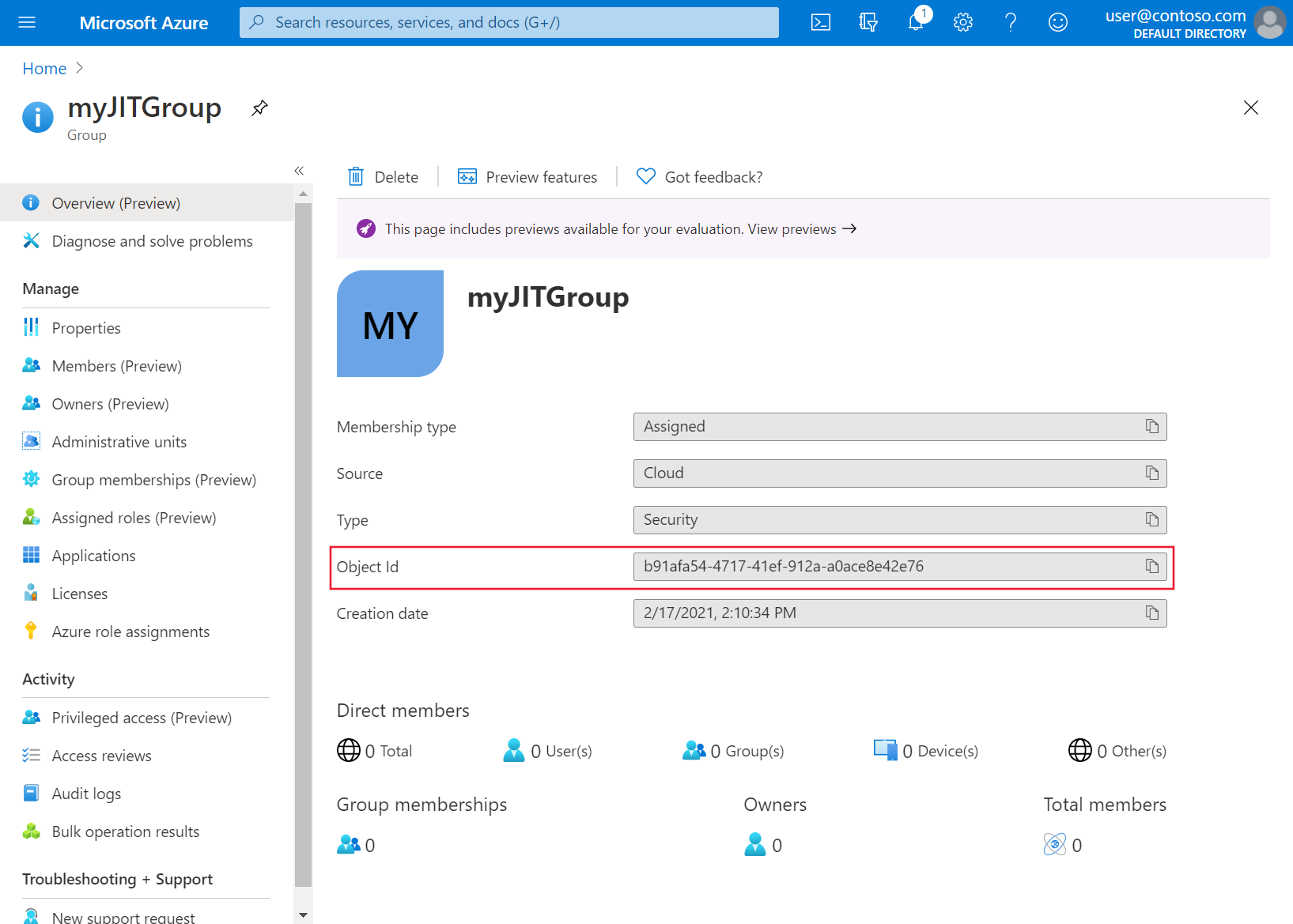
结合
--aad-admin-group-objects-ids和--aad-tenant-id parameters使用az aks create命令创建 AKS 群集与 AKS 托管 Azure AD 的集成,并包含在前面步骤中记下的值。az aks create -g myResourceGroup -n myManagedCluster --enable-aad --aad-admin-group-object-ids <object-id> --aad-tenant-id <tenant-id>在 Azure 门户中,选择“活动”>“特权访问(预览版)”>“启用特权访问”。
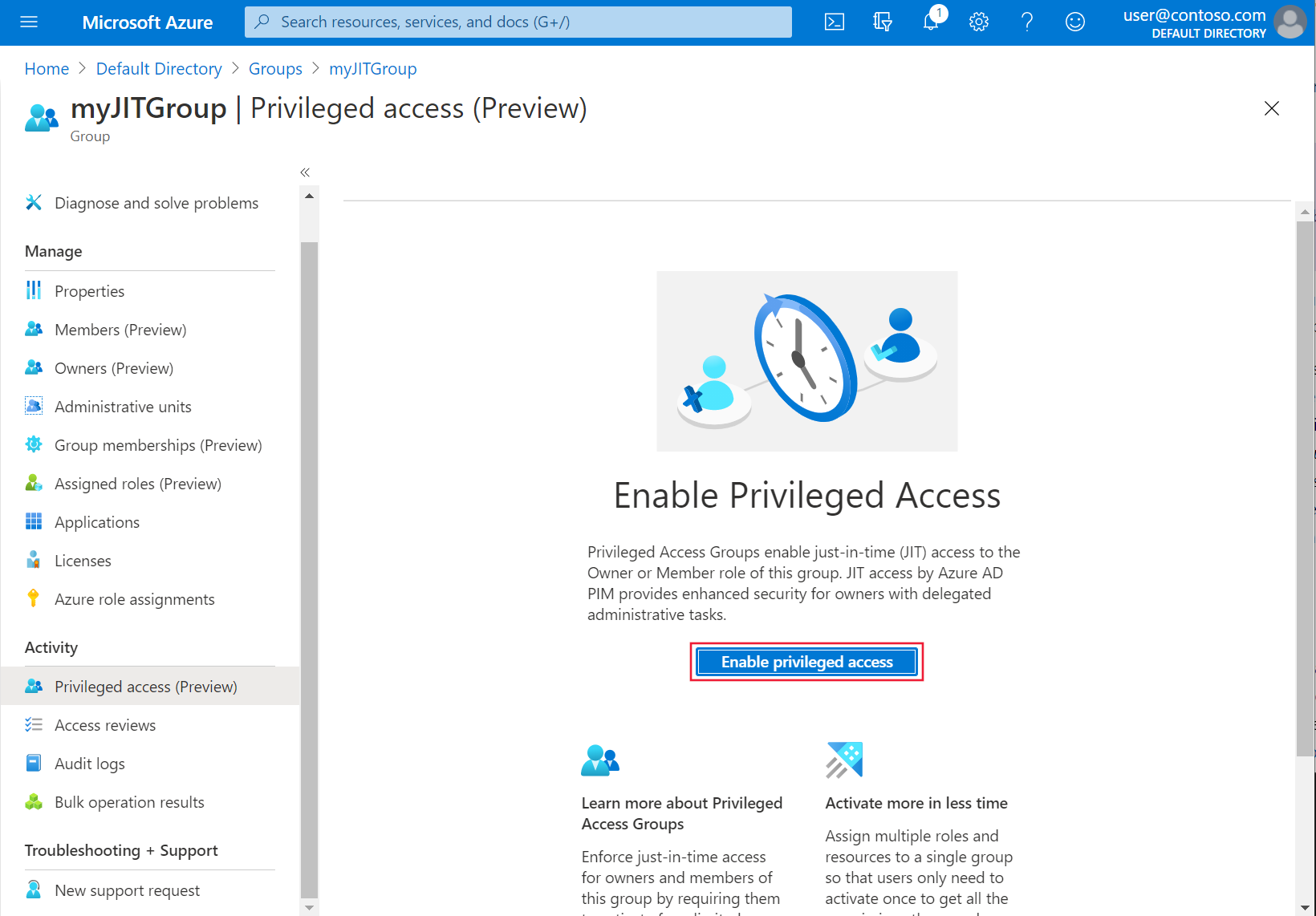
若要授予访问权限,请选择“添加分配”。
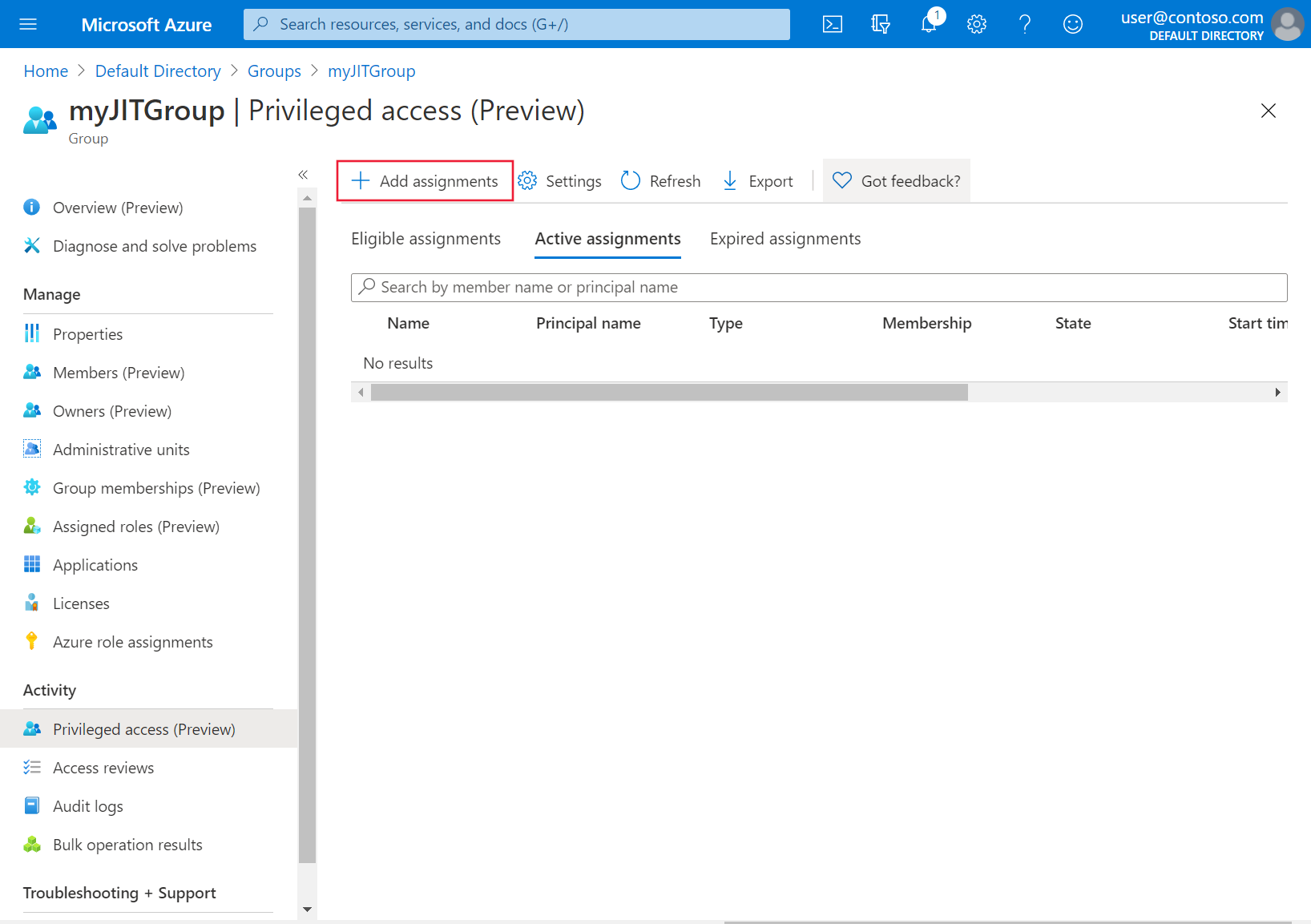
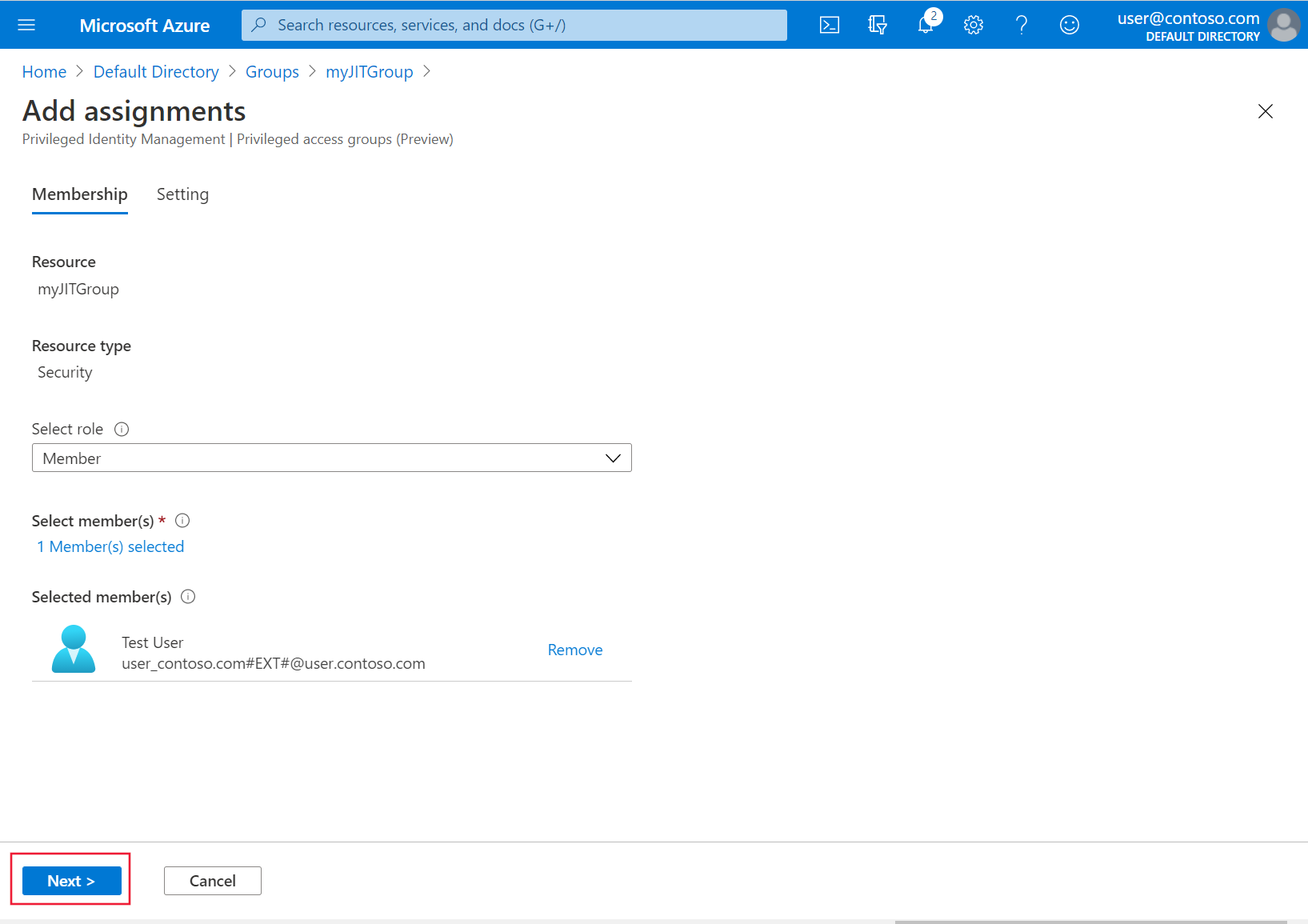
从“选择角色”下拉列表中,选择要为其授予群集访问权限的用户和组。 组管理员随时可以修改这些分配。 然后,选择“下一步”。
在“分配类型”下选择“活动”,然后指定所需的持续时间。 提供理由,然后选择“分配”。 有关分配类型的详细信息,请参阅在 Privileged Identity Management 中为特权访问组分配资格(预览版)。
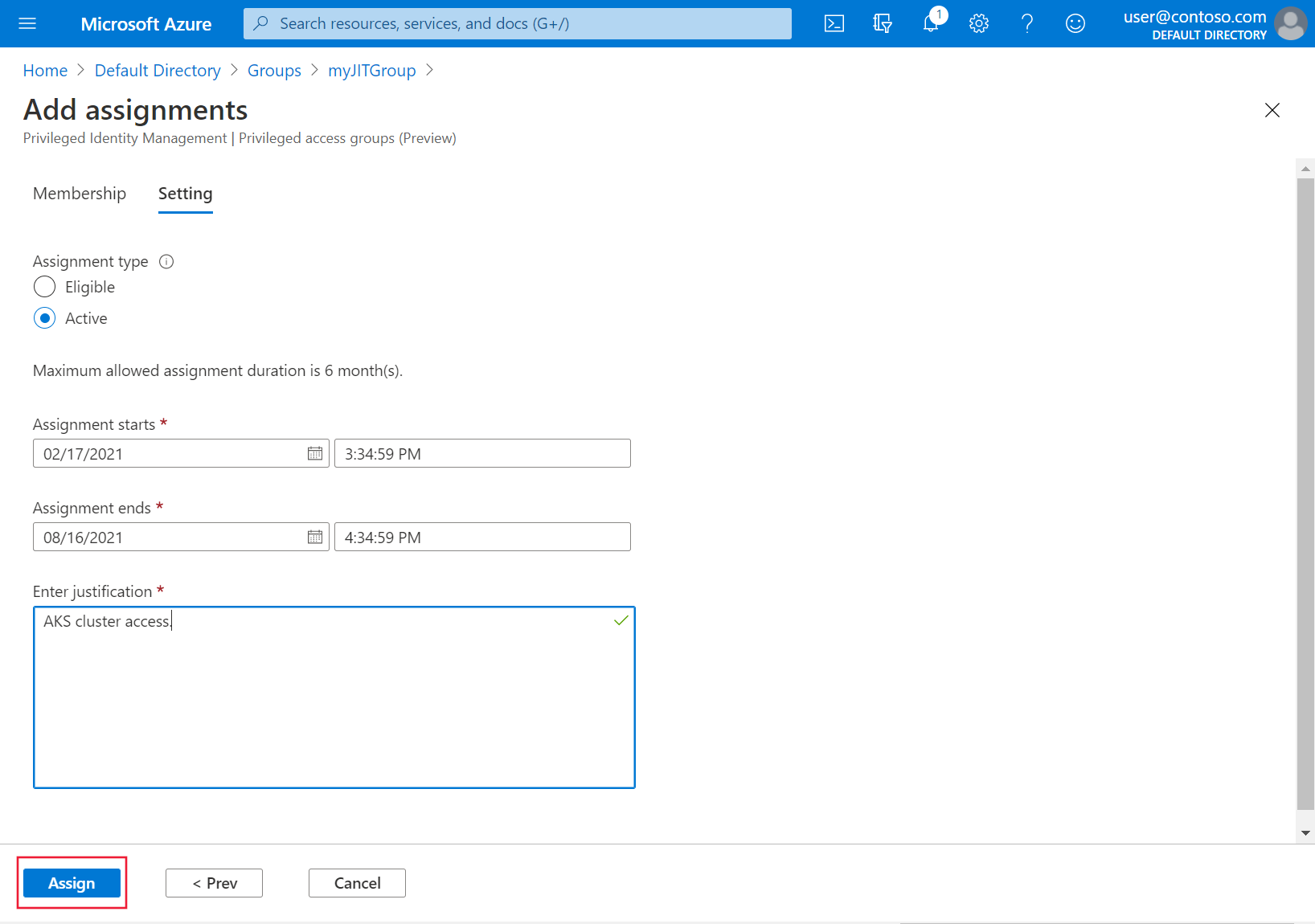
完成分配后,通过访问群集来验证是否即时访问是否运行正常:
使用
az aks get-credentials命令获取用户凭据以访问群集。az aks get-credentials --resource-group myResourceGroup --name myManagedCluster按照以下步骤登录。
使用
kubectl get nodes命令查看群集中的节点。kubectl get nodes请注意身份验证要求,并按照步骤完成身份验证。 如果成功,应会看到类似于以下示例输出的输出:
To sign in, use a web browser to open the page https://microsoft.com/deviceloginchina and enter the code AAAAAAAAA to authenticate. NAME STATUS ROLES AGE VERSION aks-nodepool1-61156405-vmss000000 Ready agent 6m36s v1.18.14 aks-nodepool1-61156405-vmss000001 Ready agent 6m42s v1.18.14 aks-nodepool1-61156405-vmss000002 Ready agent 6m33s v1.18.14
在命名空间级别应用即时访问
将 AKS 群集与 Azure RBAC 集成。
通过角色分配将要与即时访问集成的组与群集中的命名空间相关联。
az role assignment create --role "Azure Kubernetes Service RBAC Reader" --assignee <AAD-ENTITY-ID> --scope $AKS_ID/namespaces/<namespace-name>将在命名空间级别配置的组与 PIM 相关联以完成配置。
疑难解答
如果 kubectl get nodes 返回类似于下面的错误:
Error from server (Forbidden): nodes is forbidden: User "aaaa11111-11aa-aa11-a1a1-111111aaaaa" cannot list resource "nodes" in API group "" at the cluster scope
请确保安全组的管理员为你的帐户提供了“活动”分配。
后续步骤
- 了解用于 Kubernetes 授权的 Azure RBAC 集成。
- 了解 Azure AD 与 Kubernetes RBAC 的集成。
- 使用 kubelogin 来访问 kubectl 中未提供的 Azure 身份验证功能。
- 详细了解 AKS 和 Kubernetes 标识概念。