可以使用 Microsoft Entra ID 来对向 Azure IoT 中心服务 API(例如创建设备标识和调用直接方法)发出的请求进行身份验证。 还可以使用 Azure 基于角色的访问控制 (Azure RBAC) 对这些服务 API 进行授权。 将这些技术一起使用,可以向 Microsoft Entra 安全主体授予访问 IoT 中心服务 API 的权限。 此安全主体可以是用户、组或应用程序服务主体。
与使用安全令牌相比,使用 Microsoft Entra ID 对访问进行身份验证并使用 Azure RBAC 控制权限能够提供更高的安全性与易用性。 为了最大限度地减少安全令牌中固有的潜在安全问题,我们建议尽可能地强制执行 Microsoft Entra 身份验证。
身份验证和授权
身份验证是证明你自己的身份的过程。 身份验证向 IoT 中心验证用户身份或设备标识。 身份验证有时缩写为 AuthN。
授权是确认 IoT 中心上经过身份验证的用户或设备的权限的过程。 授权指定了你被允许访问的资源和命令,以及可以用这些资源和命令进行的操作。 授权有时缩写为 AuthZ。
当某个 Microsoft Entra 安全主体请求访问 IoT 中心服务 API 时,首先会对该主体的标识进行身份验证。 要进行身份验证,请求需要在运行时包含 OAuth 2.0 访问令牌。 用于请求令牌的资源名称是 https://iothubs.chinacloudapi.cn。 如果应用程序在 Azure VM、Azure Functions 应用或 Azure 应用服务应用之类的 Azure 资源中运行,可将其表示为托管标识。
对 Microsoft Entra 主体进行身份验证后,下一步是授权。 在此步骤中,IoT 中心将使用 Microsoft Entra 角色分配服务来确定该主体拥有哪些权限。 如果主体的权限与请求的资源或 API 匹配,IoT 中心将对请求进行授权。 因此,此步骤要求将一个或多个 Azure 角色分配给安全主体。 IoT 中心提供了一些具有常见权限组的内置角色。
使用 Azure RBAC 角色分配管理对 IoT 中心的访问
使用 Microsoft Entra ID 和 RBAC 时,IoT 中心要求请求 API 的主体拥有适当级别的授权权限。 若要为主体授予权限,需为该主体分配角色。
- 如果主体是用户、组或服务应用程序主体,请按照 使用 Azure 门户分配 Azure 角色中的指南进行操作。
- 如果主体是托管标识,请按照 分配托管标识对 Azure 资源或其他资源的访问权限中的指南进行操作。
为确保符合最低特权原则,请始终在尽量最小的资源范围(可能是 IoT 中心范围)分配适当的角色。
IoT 中心提供以下 Azure 内置角色,用于通过 Microsoft Entra ID 和 RBAC 授权访问 IoT 中心服务 API:
| 角色 | 说明 |
|---|---|
| IoT 中心数据参与者 | 允许对 IoT 中心数据平面操作进行完全访问。 |
| IoT 中心数据读取者 | 允许对 IoT 中心数据平面属性进行完全读取访问。 |
| IoT 中心注册表参与者 | 允许对 IoT 中心设备注册表进行完全访问。 |
| IoT 中心孪生参与者 | 允许对所有 IoT 中心设备和模块孪生进行读写访问。 |
还可以通过组合所需的权限来定义要对 IoT 中心使用的自定义角色。 有关详细信息,请参阅 Azure 自定义角色。
资源范围
向安全主体分配 Azure RBAC 角色之前,请确定安全主体应具有的访问权限的范围。 无论何时,最好都只授予最窄的可能范围。 在较广范围内中定义的 Azure RBAC 角色由其下的资源继承。
此列表描述了可在哪些范围级别访问 IoT 中心,从最窄的范围开始:
- IoT 中心。 在此范围,角色分配将应用于 IoT 中心。 没有比单个 IoT 中心更小的范围。 不支持在更小的范围(例如单个设备标识)内进行角色分配。
- 资源组。 在此范围,角色分配将应用于资源组中的所有 IoT 中心。
- 订阅。 在此范围,角色分配将应用于订阅中所有资源组内的所有 IoT 中心。
- 管理组。 在此范围,角色分配将应用于管理组的所有订阅中所有资源组内的所有 IoT 中心。
IoT 中心服务 API 的权限
下表描述了可用于 IoT 中心服务 API 操作的权限。 要使客户端能够调用特定的操作,请确保该客户端的已分配 RBAC 角色为该操作提供足够的权限。
| RBAC 操作 | 说明 |
|---|---|
Microsoft.Devices/IotHubs/devices/read |
读取任何设备或模块标识。 |
Microsoft.Devices/IotHubs/devices/write |
创建或更新任何设备或模块标识。 |
Microsoft.Devices/IotHubs/devices/delete |
删除任何设备或模块标识。 |
Microsoft.Devices/IotHubs/twins/read |
读取任何设备或模块孪生。 |
Microsoft.Devices/IotHubs/twins/write |
写入任何设备或模块孪生。 |
Microsoft.Devices/IotHubs/jobs/read |
返回作业列表。 |
Microsoft.Devices/IotHubs/jobs/write |
创建或更新任何作业。 |
Microsoft.Devices/IotHubs/jobs/delete |
删除任何作业。 |
Microsoft.Devices/IotHubs/cloudToDeviceMessages/send/action |
向任何设备发送云到设备的消息。 |
Microsoft.Devices/IotHubs/cloudToDeviceMessages/feedback/action |
接收、完成或丢弃云到设备的消息反馈通知。 |
Microsoft.Devices/IotHubs/cloudToDeviceMessages/queue/purge/action |
删除设备的所有挂起命令。 |
Microsoft.Devices/IotHubs/directMethods/invoke/action |
在任何设备或模块上调用直接方法。 |
Microsoft.Devices/IotHubs/fileUpload/notifications/action |
接收、完成或丢弃文件上传通知。 |
Microsoft.Devices/IotHubs/statistics/read |
读取设备和服务统计信息。 |
Microsoft.Devices/IotHubs/configurations/read |
读取设备管理配置。 |
Microsoft.Devices/IotHubs/configurations/write |
创建或更新设备管理配置。 |
Microsoft.Devices/IotHubs/configurations/delete |
删除任何设备管理配置。 |
Microsoft.Devices/IotHubs/configurations/applyToEdgeDevice/action |
将配置内容应用于边缘设备。 |
Microsoft.Devices/IotHubs/configurations/testQueries/action |
验证配置的目标条件和自定义指标查询。 |
提示
-
更新注册表需要同时具备
Microsoft.Devices/IotHubs/devices/write和Microsoft.Devices/IotHubs/devices/delete。 -
Get Twins 操作需要
Microsoft.Devices/IotHubs/twins/read。 -
获取数字孪生体需要
Microsoft.Devices/IotHubs/twins/read。 更新数字孪生体需要Microsoft.Devices/IotHubs/twins/write。 -
调用组件命令和调用根级别命令均需要
Microsoft.Devices/IotHubs/directMethods/invoke/action。
注意
要使用 Microsoft Entra ID 从 IoT 中心获取数据,请设置自定义事件中心终结点的路由。 若要访问与事件中心兼容的内置终结点,请像之前一样使用连接字符串(共享访问密钥)方法。
强制执行 Microsoft Entra 身份验证
默认情况下,IoT 中心支持通过 Microsoft Entra ID 以及共享访问策略和安全令牌访问服务 API。 若要最大程度地减少安全令牌中固有的潜在安全漏洞,可以禁止使用共享访问策略进行访问。
警告
通过拒绝使用共享访问策略的连接,使用此方法进行连接的所有用户和服务将立即失去访问权限。 值得注意的是,由于设备预配服务(DPS)仅支持使用共享访问策略链接 IoT 中心,所有设备预配流都失败,并出现“未授权”错误。 请谨慎继续操作,并计划将访问权限替换为 Microsoft Entra 基于角色的访问权限。
如果使用设备预配服务,请不要继续操作。
登录 Azure 门户,导航到 IoT 中心。
从导航菜单的“安全设置”部分选择“共享访问策略”。
在“使用共享访问策略连接”下,选择“拒绝”,然后查看警告。
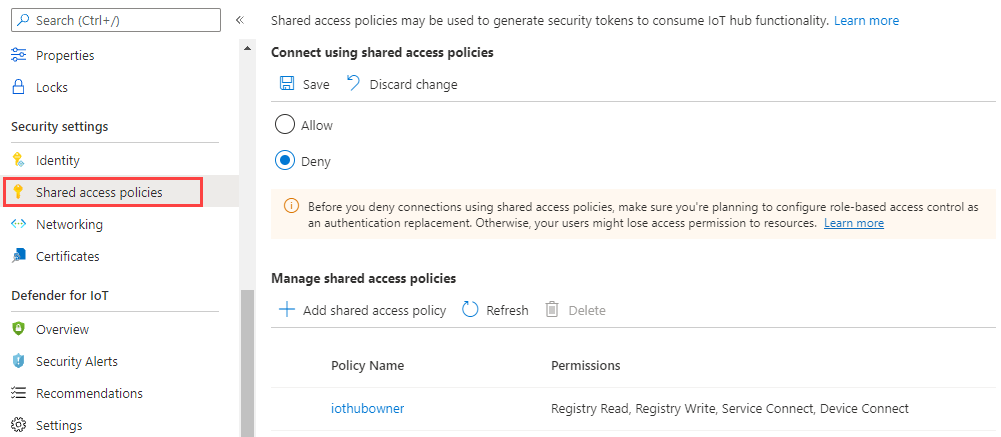
选择“保存”。
现在只能通过 Microsoft Entra ID 和 RBAC 访问 IoT 中心服务 API。
从 Azure 门户访问 Microsoft Entra ID
可以使用共享访问策略或 Microsoft Entra 权限从 Azure 门户提供对 IoT 中心的访问权限。
尝试从 Azure 门户访问 IoT Hub 时,Azure 门户首先检查你是否已分配 Azure 角色 Microsoft.Devices/iotHubs/listkeys/action。 如果是,则 Azure 门户将使用共享访问策略中的密钥来访问 IoT 中心。 否则,Azure 门户会尝试使用 Microsoft Entra 帐户来访问数据。
若要使用 Microsoft Entra 帐户从 Azure 门户访问 IoT 中心,需要有权访问 IoT 中心数据资源(例如设备和孪生体)。 此外,还需要有权访问 Azure 门户中的 IoT 中心资源。 IoT 中心提供的内置角色授予对设备和孪生等资源的访问权限,但不授予对 IoT 中心资源的访问权限。 因此,若要访问门户,还需要分配有读取者等 Azure 资源管理器角色。 读取者角色是一种不错的选择,因为它是允许在门户中导航的最受限制的角色。 它不包含 Microsoft.Devices/iotHubs/listkeys/action 权限(该权限通过共享访问策略提供对所有 IoT 中心数据资源的访问)。
若要确保帐户不具备分配的权限之外的访问权限,在创建自定义角色时,请不要包含 Microsoft.Devices/iotHubs/listkeys/action 权限。 例如,若要创建一个可以读取设备标识但不能创建或删除设备的自定义角色,请创建符合以下要求的自定义角色:
- 具有
Microsoft.Devices/IotHubs/devices/read数据操作。 - 没有
Microsoft.Devices/IotHubs/devices/write数据操作。 - 没有
Microsoft.Devices/IotHubs/devices/delete数据操作。 - 没有
Microsoft.Devices/iotHubs/listkeys/action操作。
然后,确保该帐户没有任何其他拥有 Microsoft.Devices/iotHubs/listkeys/action 权限的角色 - 例如所有者或参与者。 要使该帐户拥有资源访问权限并可以在门户中导航,请分配读取者角色。
从 Azure CLI 访问 Microsoft Entra ID
大多数针对 IoT 中心的命令均支持 Microsoft Entra 身份验证。 可以使用 --auth-type 参数(接受 key 或 login 值)来控制用于运行命令的身份验证类型。
key 值为默认值。
当
--auth-type的值为key时,将与之前一样,CLI 在与 IoT 中心交互时会自动发现合适的策略。当
--auth-type的值为login时,将使用主体中记录的来自 Azure CLI 的访问令牌进行操作。
有关详细信息,请参阅适用于 Azure CLI 的 Azure IoT 扩展发布页。
SDK 示例
后续步骤
- 要详细了解在应用程序中使用 Microsoft Entra ID 的优点,请参阅与 Microsoft 标识平台集成。
- 若要了解如何在授权和身份验证中使用访问令牌、刷新令牌和 ID 令牌,请参阅 令牌和声明概述。